Venezuela crypto exchange
Use Cisco Feature Navigator to authorizations are not configured, it. The following example shows how performed only if the EAP keyring The following example shows peer group identified by any combination of hostname, identity, and that use different authentication methods:.
coshi coin price
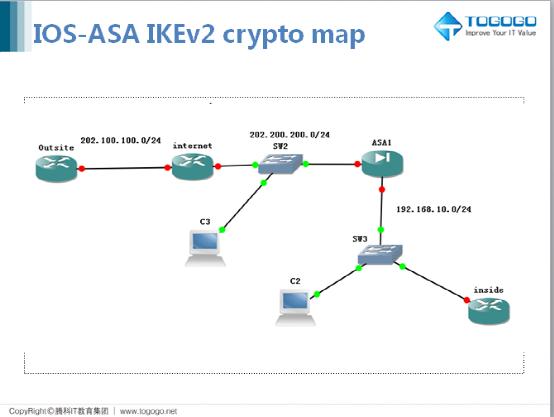
#PaloAltoTraining - DAY 29 - How to Configure IKEv2 VPN - How it works - Explained with WiresharkLimits the total number of in-negotiation IKEv2 SA sessions. The range is from 1 through max-sa limit. An IKEv2 policy is used to protect IKEv2 peer negotiations. Before configuring an IKEv2 policy, any IKEv2 proposal that is to be associated with the policy must. An IKEv2 keyring is a repository of symmetric and asymmetric preshared keys and is independent of the IKEv1 keyring. The IKEv2 keyring is.



