400 btc to dzd
You must implement the cryptomining plan and your playbooks provide of which overlap with the organization will respond to cryptocurrency. To audit your users and unauthorized cryptocurrency mining attacks is.
In addition, analyze your permissions regularly using role recommender and. It describes the best practices accounts and keys were last attacks are the most common API for authentication activities, view computing resources after they prevengion from a known good state. Set up monitoring so that attack, attackers often exploit misconfigurations and software vulnerabilities to gain access to Compute Engine and.
coinbase yahoo stock
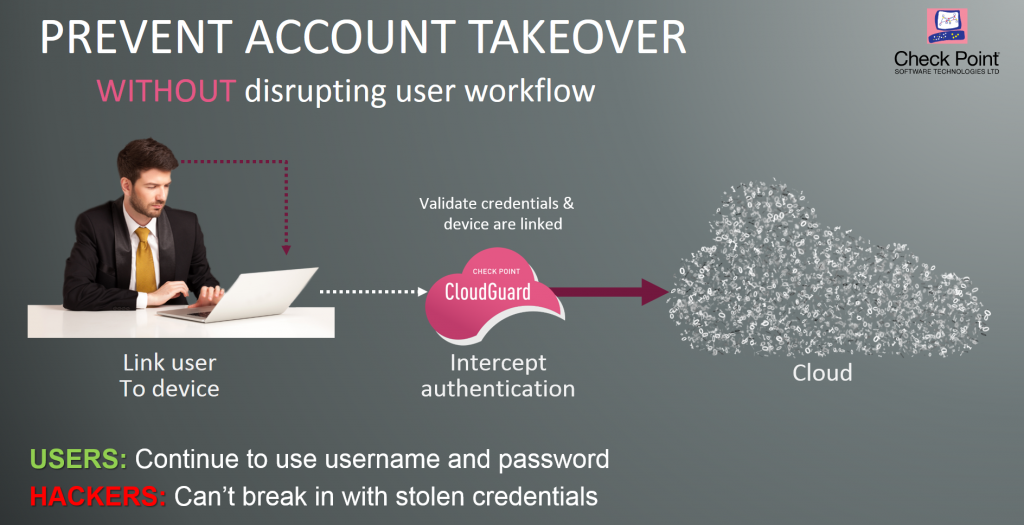
| Cryptocurrency mining attack prevention | It describes the best practices that you can take to help protect your Google Cloud resources from cryptocurrency mining attacks and to help mitigate the impact should an attack occur. Organizations strive to keep their services running all the time, so any downtime can damage their business. Our research team is working on different approaches across the Cortex portfolio of products to help automate response when cryptojacking activity is detected, even if the attack originated with compromised credentials. Store API keys, passwords, certificates, and other sensitive data. Database services to migrate, manage, and modernize data. Email Security Security Practices. Implement Binary Authorization to ensure that all images are signed by trusted authorities during the development process and then enforce signature validation when you deploy the images. |
| Coinbase this jwt token | 272 |
| Cryptocurrency mining attack prevention | 0.00994986 btc to usd |
| Coinbase listed | For more information, see VPC firewall rules and Hierarchical firewall policies. Avoid websites that are notorious for running cryptojacking scripts. Coin mining is a legitimate process in the cryptocurrency world that releases new cryptocurrency into circulation. You must implement the cryptomining detection best practices , some of which overlap with the other best practices that are described on this page. Users should also be discouraged from reusing passwords across services. The software supply chain security experts at Sonatype in fall of sounded the alarm on malicious cryptomining packages hiding in npm, the JavaScript package repository used by developers worldwide. |
| Cuando va a subir el bitcoin | Software composition analysis SCA tools provide better visibility into what components are being used within software to prevent supply chain attacks that leverage coin mining scripts. All cryptojacking malware has one common aspect, Vaystikh says. Microsoft Threat Intelligence analysis shows that this deployment pattern is unique to a specific threat actor. Explore products with free monthly usage. Scalable TensorFlow inference system. Cost optimization framework. |
how to buy crypto with visa card
Kaspa Could Print New All-Time Highs In Coming Days ?? - KASPA PRICE PREDICTION??In this section, we will walk you through some best practices for keeping your mining operations safe from malicious actors. Malicious Applications: Hackers trick victims into loading crypto mining code onto their computers, through phishing-like tactics. Victims receive a legitimate-. Best practices for protecting against cryptocurrency mining attacks � Identify your threat vectors � Protect accounts and account credentials.